RED TEAMING – ADVANCED OFFENSIVE SKILLS FOR IT & SOC
The training provides professionals working in IT and SOC departments with the skills necessary to independently test their organization’s cybersecurity in the same way cybercriminals do during real-world corporate breaches. Additionally, it helps participants better prepare for handling cyber incidents in accordance with the requirements of the new cybersecurity regulations. It also enables organizations to build their own Red Team units in a short time.

Rapid acquisition of advanced offensive skills (red teaming, hacking) is made possible by providing learners with specialized educational tools:
Cyber Range – a network infrastructure, Active Directory, and IT and OT systems operating similarly to a real corporate IT environment, where participants can practice realistic cyberattack scenarios.
Cyber Soldier –a GUI application with an extensive knowledge base that supports the execution of advanced cyberattack scenarios in the same way cybercriminals operate.
A key feature and benefit of the training is its realism, entirely based on cyber threat intelligence.
A key feature and benefit of the training is its realism, entirely based on cyber threat intelligence. The course does not involve fictional CTF challenges - all cyberattack scenarios are grounded in real-world activities of cybercriminal groups, as documented in credible sources (e.g., CERT reports and post-breach analysis by leading cybersecurity firms). Exercises are conducted in environments with active antivirus protection, replicating real corporate IT systems.
PREPARATION FOR DORA, GDPR, AND NIS2 REQUIREMENTS
Managing cybersecurity incidents is a legal obligation for nearly every organization in EU. In the event of a significant incident, post-breach analysis often involves all IT staff - not just SOC teams (e.g., application and database administrators may need to verify whether customer data was leaked). Red teaming training provides IT and SOC professionals with a clear understanding of what a real breach looks like - it’s not just about running automatic scanners and searching for exploits.
BUILDING AN INTERNAL RED TEAM
This training helps financial sector organizations prepare their internal red team testers. The DORA regulation allows Threat-Led Penetration Testing (TLPT) to be conducted by in-house teams under certain conditions. TLPT should be performed using threat scenarios aligned with the TIBER-EU (Threat Intelligence-based Ethical Red Teaming) guidelines.
PREPARATION FOR PRACTICAL RED TEAM CERTIFICATION EXAMS
Realistic cyberattack exercises in Active Directory environments with active antivirus protection are invaluable for individuals preparing for practical exams such as OffSec Certified Professional (OSCP) and OffSec Experienced Penetration Tester (OSEP).
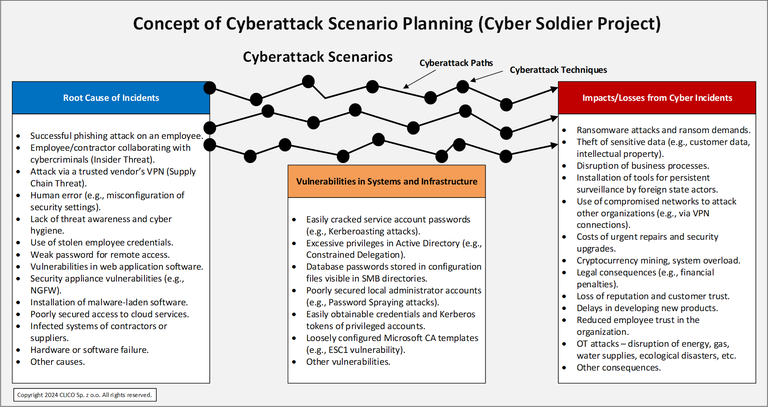
IDENTIFYING VULNERABILITIES EXPLOITED BY CYBERCRIMINALS
The training provides the skills needed to independently test the effectiveness of an organization’s cybersecurity. Cybercriminals often exploit vulnerabilities during real-world breaches that scanners cannot detect, such as:
- Excessive privileges in Active Directory (e.g., service accounts in the Account Operators group or with Constrained Delegation privileges).
- Easily accessible privileged credentials and Kerberos tokens.
- Weak service account passwords (e.g., via Kerberoasting attacks).
- Database passwords stored in configuration files exposed on SMB directories.
- Poorly secured local administrator accounts (e.g., Password Spraying attacks).
- Misconfigured Microsoft CA templates (e.g., ESC1 vulnerability allowing domain admin certificate generation).
Early detection and remediation of vulnerabilities exploited by cybercriminals bring significant benefits to organizations - preventing attackers from achieving their objectives and avoiding losses from ransomware and other cyber incidents.
Ćwiczenia zaawansowanych scenariuszy cyberataków odbywają się z użyciem aplikacji Cyber Soldier. Jest to aplikacja edukacyjna, która pomaga specjalistom IT nie posiadającym głębokiej wiedzy ofensywnej (red team, hacking) w wykonaniu realnych scenariuszy włamań do systemów informatycznych. Wszystkie scenariusze włamań są oparte na wiarygodnych źródłach z wywiadu cybernetycznego (Threat Intelligence) - scenariusze cyberataków są realistyczne, aplikacja Cyber Soldier Project zachowuje się jak prawdziwi cyberprzestępcy. Przy tym nie jest to "automat black box" - aplikacja Cyber Soldier Project pokazuje i tłumaczy ludziom jak przebiegają rzeczywiste scenariusze włamań.
cyber soldier project
RED TEAMING FOR IT & SOC – TRAINING PROGRAM
PREPARATION
Introduction to Red Teaming and Adversary Emulation.
Overview of Cyber Range and Cyber Soldier offensive tools.
Exercises in basic offensive skills in the Cyber Range – Parts 1, 2, and 3.
BASIC MODULE
Scenario 1: Active Directory reconnaissance.
Scenario 2: Network reconnaissance (SSH services, SMB shares, Web directories, databases).
Scenario 3: Cracking Windows domain service account passwords (Kerberoasting).
Scenario 4 (slow option): Cracking Windows domain service account passwords (Kerberoasting).
Scenario 5: Searching for credentials and sensitive data in SMB network directories.
Scenario 6: Exploiting SMB vulnerabilities on legacy Windows servers – MS17-010 Eternal.
Scenario 7: Password spraying on domain accounts.
Scenario 8: Password spraying on local administrator accounts.
Scenario 9: Password spraying on Linux systems.
Scenario 10: Password spraying on MS SQL databases.
Scenario 11: Password spraying on MySQL databases.
Scenario 12: Deploying a Web Shell via editable SMB share on a Web server to execute OS commands.
Scenario 13: Dumping Windows credentials using a Web Shell and service account privilege escalation.
Scenario 14: Bypassing AV/EDR using local admin accounts.
Scenario 15: Extracting SAM credentials with admin password or NTLM hash.
Scenario 16: Dumping LSASS credentials with admin password or NTLM hash.
Scenario 17: Exploiting Microsoft Certificate Authority (MSCA) to obtain domain admin privileges.
Scenario 18: Capturing Net-NTLMv2 credentials on the network and performing SMB relaying.
Scenario 19: Lateral movement to Windows systems using various protocols (SMB, WinRM, WMI, RDP).
Scenario 20: Using Backup Operators privileges to extract domain account credentials (SAM, DCSync).
Scenario 21: Exploiting Constrained Delegation to gain Windows admin access.
Scenario 22: Leveraging Account Operators group privileges to read LAPS (local admin accounts).
Scenario 23: Leveraging Account Operators group privileges to access gMSA (service accounts).
Scenario 24: Stealing Kerberos tokens and moving laterally with privileged account tokens.
Scenario 25: Bypassing AV/EDR and escalating service account privileges to Windows admin (SYSTEM level).
Scenario 26: Command and Control – tunneling attacks into the internal network via SOCKS Proxy.
Scenario 27: Reconnaissance of Web services within the network.
Scenario 28: Exploiting WordPress to deploy a Web Shell and execute OS commands.
Scenario 29: Password spraying attacks on Postgres databases.
Scenario 30: Password spraying attacks on Oracle databases.
ADVANCED MODULE (Optional Based on Group Level)
Scenario 31: Red Teaming with Sliver Command and Control – Antivirus Evasion, Launching the Sliver Implant
Scenario 32: Red Teaming with Sliver Command and Control – Antivirus Evasion, Tunneling Attacks from C&C to the Internal Network
Scenario 33: Red Teaming with Sliver Command and Control – Antivirus Evasion, Credential Theft Using Various Techniques (e.g., BOF/COFF, Execute Assembly)
Scenario 34: Red Teaming with Meterpreter Command and Control – Antivirus Evasion, Launching the Meterpreter Implant
Scenario 35: Red Teaming with Meterpreter Command and Control – Antivirus Evasion, Tunneling Attacks from C&C to the Internal Network
Scenario 36: Red Teaming with Meterpreter Command and Control – Antivirus Evasion, Credential Theft Using Various Techniques (e.g., Process Injection/Migrate, Execute Binary from Memory)
DURATION
3 days with an instructor + 5 days of remote access to the lab and Cyber Soldier application
PRICE 3900 PLN / participant
The "Red Teaming for IT & SOC" training is an excellent preparation for practical cybersecurity assessments using the Cyber Soldier Project tools.