CYBER SOLDIER PROJECT
The environment and tools of the Cyber Soldier Project were created for IT and SOC personnel, with the goal of enabling them to quickly develop offensive skills (hacking, Red Team). These competencies are essential for proper incident response and participation in post-incident investigations, where understanding cybercriminal activity is crucial. The tools also allow users to independently test the effectiveness of their organization’s cybersecurity systems (including AV/EDR, SIEM) by simulating realistic cyberattack scenarios.

Response to threats and the new cybersecurity legislation.
A quick and effective response to cyber incidents allows organizations to minimize or even avoid losses. Incident management is required by law, including regulations such as the NIS2 Directive, DORA, and GDPR. The ability to identify and respond to cyber incidents is essential for many employees working in IT and OT environments — incident response typically involves, among others:
- Security administrators
- Network and IT systems administrators
- Application and database administrators
- Security team specialists
- SOC/CSIRT operators and analysts
- OT specialists
The following tools are available to IT and SOC personnel:
Cyber Range – A simulated environment including network infrastructure, Active Directory, and both IT and OT systems protected by commercial security solutions such as EDR and NGFW. This setup serves as a hands-on learning platform for Incident Response. Training is conducted using the same EDR and NGFW tools that participants use in their own organizations.
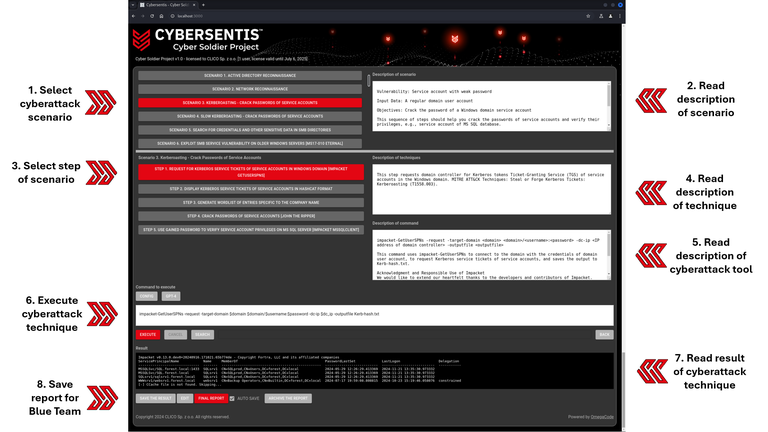
Cyber Soldier – The educational application supports users in executing realistic, advanced cyberattack scenarios fully based on Threat Intelligence — both in training environments and, where applicable, in production systems. The attack techniques are carried out using the best legally available tools, often identical to those used in real-world cyberattacks.
The Cyber Soldier application was developed by Omega Code Sp. z o.o.
Methodology for Building Incident Response Competencies
Stage 1: Incident Response Training in the Cyber Range (training lab)
The Cyber Range environment is designed to replicate a real-world IT infrastructure and includes components most commonly targeted by cybercriminals, such as Active Directory, MS Exchange, MS SQL, MS Certificate Authority, MySQL, web applications, and Linux servers. These systems are protected by widely used commercial security solutions, including Check Point, CyberArk, Palo Alto Networks, SentinelOne, and Trend Micro.
The Cyber Range is available to training participants both on-site at the CLICO training center and remotely, 24/7.
Stage 2: Incident Response Training in a Production Environment
The most effective way to learn how to respond to cyber incidents is by simulating real cyberattacks within the company’s production environment and involving those responsible for cybersecurity management in the response process. There’s no need to wait for an actual breach — the Cyber Soldier application enables safe and controlled execution of realistic cyberattack scenarios in live networks. This allows participants to practice incident response using the tools already deployed in their organization, such as EDR, NGFW, SIEM, and others.
INCIDENT RESPONSE IN PRODUCTION ENVIRONMENTS
Advanced Offensive Skills for IT and SOC Teams
Cyber Soldier is an educational application designed to support IT and SOC specialists who do not yet have advanced offensive knowledge (e.g. red teaming or hacking) in learning and executing realistic cyber intrusion scenarios. All scenarios are based on credible Threat Intelligence sources and reflect real-world cybercriminal tactics — the application does not rely on made-up, CTF-style challenges. Cyber Soldier behaves like real cyber attackers, but it is not just a ‘black-box automation’ tool — it guides users step by step through real attack scenarios, explaining each stage along the way. It’s an ideal solution for preparing internal Red Team capabilities.
Combined Offensive and Defensive Capabilities
The Cyber Soldier project is carried out by a team of cybersecurity experts who combine advanced offensive and defensive skills, confirmed by widely recognized certifications.
Offensive Capabilities:
- Offsec Experienced Penetration Tester (OSEP)
- OffSec Web Expert (OSWE)
- OffSec Certified Professional (OSCP)
- EC-Council Certified Ethical Hacker (CEH) Master – certified instructors
Defensive Capabilities:
- (ISC)² Certified Information Systems Security Professional (CISSP) – certified instructors
- EC-Council Certified Chief Information Security Officer (CCISO) – certified instructor
- AWS Certified Solutions Architect
- Certified SCADA Security Architect
- Security engineering certifications (including Check Point, Palo Alto Networks, Forescout, Forcepoint, Juniper Networks, CyberArk, F5, Imperva, Thales, and others)
The software development work in the Cyber Soldier Project was carried out by Omega Code https://omegacode.pl